Cybercriminals target the weakest link
Cybercriminals are relentless. The more a business protects themselves the more cybercriminals prey on that which the business cannot directly control – the behaviors of people! Business must invest in ongoing awareness and end-user training to ensure even this vulnerability can be minimized. Your legal practice may depend on it.
Since you don’t work in IT, it’s likely you aren’t especially fascinated by news and articles about cyber threats. Then, how could you be expected to curtail your staff’s dangerous behaviors? Just like we educate children about the possible threats from strangers or to immediately leave the house as soon as the smoke detector goes off – education and awareness of your legal team and staff against cyber threats is key for your law firm. Have you heard the phrase, “you don’t know what you don’t know?”
Internal IT departments and IT professionals
Law firms with an internal IT department should already have a heavy focus on cybersecurity. This involves a living cybersecurity plan which is then implemented for protection from, detection of and recovery from cyber threats. However, often overlooked or considered only after considerable damage has occurred is the cybersecurity awareness program as a critical component of the plan.
Since legal expertise is what your law firm does you aren’t expected to be experts on IT or cybersecurity. Outsourcing IT to a service provider specialized in cybersecurity would be wise. Besides the strategic and tactical focus on security and compliance, external IT service providers for law firms usually have cybersecurity awareness programs as part of their offerings.
If you should wish to obtain cybersecurity insurance with competitive rates, having a comprehensive cybersecurity plan that is validated and fully implemented, to include a cybersecurity awareness program for your people is essential. Insurance will only protect you after something bad has already occurred and there is no insurance provider that wants to write a policy for a law firm who has not already taken the required protective measures. You’d be considered a very high risk.
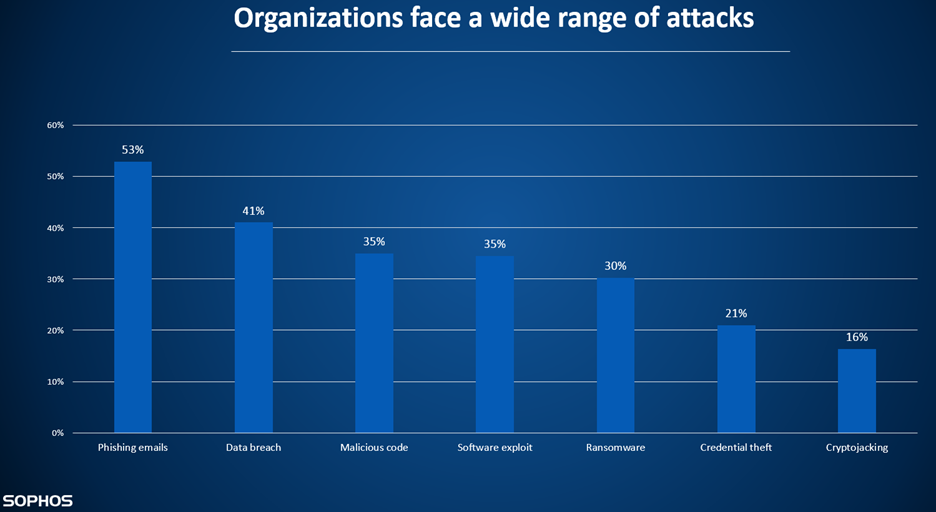
What are the most prevalent types of cybersecurity attacks?
According to SOPHOS research, 53% of attacks are related to email phishing:

Emails for example, and how end users open attachments, click on links, or share personal and confidential data are some of the risky user behaviors. Email is important to business survival so how do we reduce risk while remaining effective in our communication? The difference is increasing the user awareness of how to identify something risky and what action or behavior to take or not take!
Elements of cybersecurity awareness program
1 – Cybersecurity training as a course with a quiz (possibly a certification) that users must complete is essential. Sometimes too overwhelming for an IT department to coordinate on their own, they may hire outside consultants to assist in establishing their program. The format and length of the training course could be simple. Perhaps an internal course with online access for staff in a self-paced format with a scheduled due date would be effective. Some companies may prefer live instructor or a webinar format.
The course should be completed by every employee. All new staff should complete the training in the onboarding process. Contractors who will be given access to the network and company assets may also be required to pass a quiz before gaining their access credentials. Annually, the course should be revised for relevance and a recertification for each employee by taking another quiz is a good idea. If failed, a repeat of the course until the quiz and recertification occurs.
Yes – this diligence is necessary to reduce the vulnerabilities of human behaviors.
2 – Cybersecurity review meetings are periodic planned events where examples from the news or stories from the real world are presented, shared, and discussed as stark reminders of the invisible looming threats just waiting for someone to slip up and take the bait. Cybercriminals are relentless!
3 – Penetration testing is a technique where users receive suspicious emails as a test of what action they might take. These are done at random with no warning and simply appear along with all other emails in the inbox and during normal work activities. This is a simulation which generates a user response. Either the user reports the email as suspicious, ignores it completely, deletes it or proceeds incorrectly. Regardless of the user response the penetration test tool keeps track. Notifications and reports are then generated so feedback on trends can be given to users regularly on “why” they should have known the email was suspicious.
4 – Ongoing transparency is organic discussion. Security incidents or breaches need to be communicated for lessons learned. Proactive practice of “see something say something” and open dialogue around cybersecurity should be encouraged. A collaborative culture of learning and sharing knowledge is essential for improved cybersecurity.
The bottom line
Remember to strengthen your cybersecurity protection by mitigating risks from human behaviors. Although email is among the highest threat categories, other user behaviors around passwords, sharing devices, downloading, internet surfing and much more will be included in a cybersecurity awareness program. This should be executed as part of your broader and essential cybersecurity plan.
Always stay vigilant!
Contact us for a free assessment!
AKAVEIL Technologies, Inc. is a U.S. based IT service provider whose customer centric culture engages with your team to ensure best of class service quality and alignment. AKAVEIL offers law firm modernization with your strategic purpose in mind, from legacy technologies to the cloud and beyond. You stay focused on running your law practice while AKAVEIL ensures your business technologies are running seamlessly with reliability, security, compliance, and impeccable support response times to enhance your competitive advantage. Contact us today for a free technology assessment and build a lasting relationship with a technology partner who cares.